Secure Cloud Solutions
With innovative Automation, Security and Observability,
We help you to Design, Develop & Operate Resilient & Secure
IT infrastructure and Prevent Leakage or Loss of Data.
Defence In Depth
We provide Multiple Layers of Protection against Cyber Attacks & Misconfigurations.
- Protection with state-of-the-art Hardening Methods
- Detection with Cyber Security Intelligence & Anomally Detection Tools
- Incident Response & Automated Remediation
Cloud & Kubernetes Security
Cloud Automation & security
Cloud Automation & Security differ fundamentally from traditional on-premise approaches.
- Defining and building secure cloud with multi-layer defense strategy (Defense in Depth).
- Design aud Automate Security Incident Response in the Cloud
- Coach and transfer knowledge to your teams to assure your mid- and long-term success.

Kubernetes & Docker Security
Docker is favorite packaging micro-services tool and Kubernetes is most favorite Container run-time technology.
- Building, Hardening and Scanning Docker images
- Design Kubernetes based applications.
- Design and Operate Kubernetes Platforms.

Observability & Threat Detection Solutions
To manage your Operations and fulfill SLA, we help you to get transparency of application & infrastructure health.
- Design, Implementation & Operations of Observability Solutions.
- Innovative & Cost Effective Integration with Cloud Based Threat Detection Capabilities.
- Alerting Incident Response Processes and Automation.
Which Solutions Are You Looking For?
We can help you improve your security posture in one or more defence layers. Our solutions are:
- On one hand, leverage cloud native capabilities and hence save time and costs.
- And on the other hand, they can run on top of multiple cloud and on premise technologies.

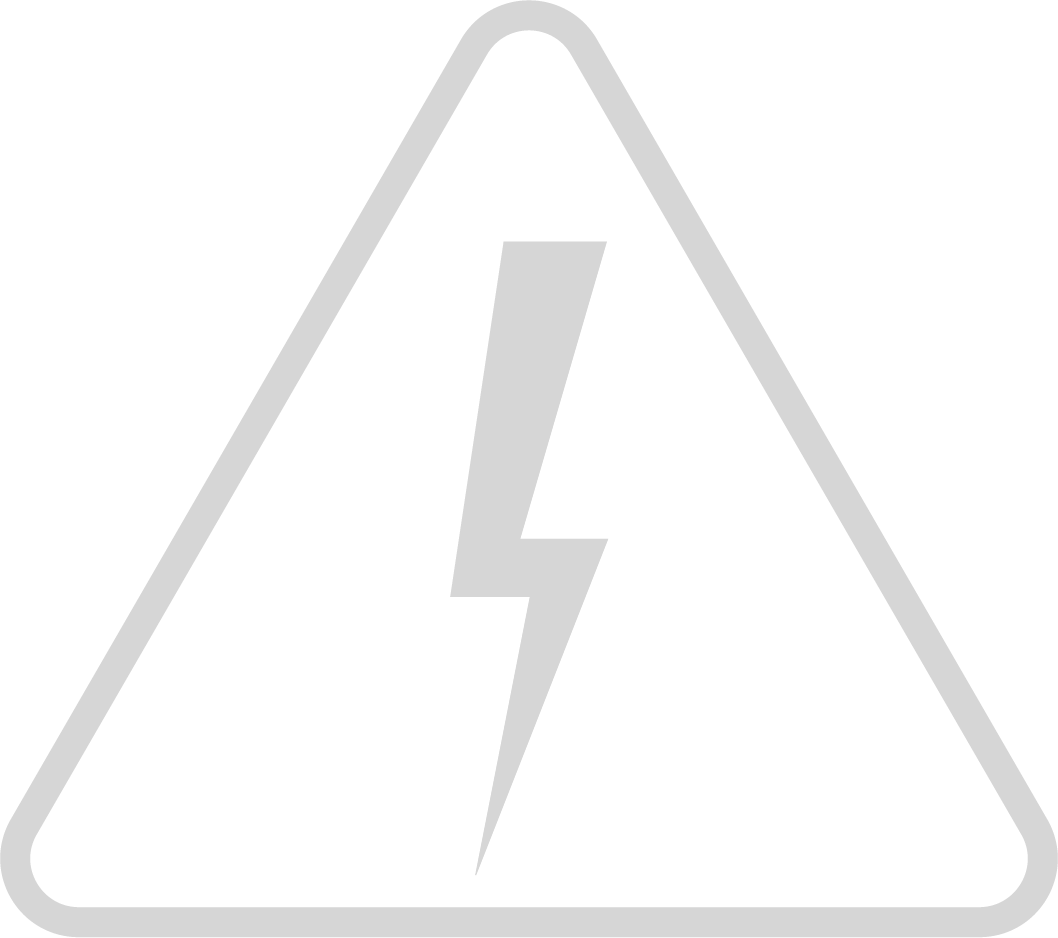
Identity & Access Management (IAM)
To prevent/minimize breaches, we design and build solid IAM solutions, with multi-layer controls.
- Cloud IAM
- Kubernetes IAM
- Zero-Trust Architecture
- Dynamic Secrets
We use state-of-the-art methods to minimize your secret management overhead.

Data Protection
We design and implement automated cloud- and on-premise solutions.
- Encryption at Rest & in Transit.
- Encryption Key & TLS Certificate Management.
- Automated Deployment and Rotation to minimize Operations Management Overhead.
To protect your data and support you to meet compliance requirements
Infrastructure Security
Our solutions for Cloud & Kubernetes minimize overhead through automating your teams’ routine activities and collecting results.
- Vulnerability Management.
- Network Security.
- Micro-Network Segmentation.
- Audit & Access Logs
- Technical Compliance Policies & Remediation.

Service Mesh
We Design and Implement Secure Solutions to connect your Cloud, IoT and On-Premise Applications:
- Data Encryption in Transit.
- Dynamic & Unique Identity for each Application.
- Control Access among Applications (App X can call App Y but not App Z)
- Automated Rotation of Secrets (Certificates, Credentials…)

Continutity Management
We design cloud and Kubernetes solutions with your SLA in mind to eliminate/minimize downtime or data loss.
- High Availability & Resilient Architectures
- Different Backup/Restore Architectures for your Environment
- Automated Software Update/Patching
- Disaster Recovery
Asset & Classification Management
To Define Risk of your Assets and make Decisions on Protection and Incident Response Activities.
- Define your Asset Categories (Infrastructure, Application, Data, Secrets,…)
- Collect Snapshots and Changes of Assets
Security Incident Response
We support you in Definition, Design and Implementation of Security Incident Response Playbooks.
- Collect and Preserve Evidence from multiple Detection Layers
- Automate Remediation to Contain Incident & Isolate Compromized Infrastructure
Zero Trust
Zero Trust can be a set of Strategies, Design Principles, Architectures and/or Tools.
For example, in the case of applications, regardless of Originating Network, our Security Architectures allow only permitted Applications to get Access to Resources & Data.
-
- Unique Identity for Each Application and Service.
- Least Privilege Access Control.
- Micro-Network Segmentation.
- Automated Creation & Rotation of Secrets
Cloud Governance at Scale
Depending on your cloud use-case you might face many challenges. We will share our experience in finding and implementing open, reliable & cost-effective solutions such as:
- Enabling tens or hundreds of development teams to be agile by using cloud infrastructure freely while maintaining security and governance.
- Definition of responsibilities of central platform teams.
- How to find a balance between cloud agility and enforcing security.
- Migrating your applications smoothly, and finding a balance between cloud native and multi-cloud/hybrid-cloud environments
- Service Mesh solutions to allow connecting cloud, IoT and on-premise applications in a controlled, secure and also agile way.
We will share our experience in finding and implementing open, reliable and cost-effective solutions.
Specific Challenges
Are You Looking For a Custom Solution?
Need Consulting? Contact Us Now!
We will be happy to listen to your challenges and wishes. Please describe briefly, how we can help you.

