Introduction
In the dynamic and fast-paced realm of container orchestration, Kubernetes has emerged as a beacon of efficiency, granting organizations the power to automate, scale, and manage applications seamlessly. But as its flames of popularity rise, they draw the shadows of cyber adversaries closer.
Using the universally recognized MITRE ATT&CK framework, we can illuminate these lurking threats, revealing the strategies attackers might employ to breach Kubernetes environments. From the innocent pull of a vulnerable Docker image to the harrowing exfiltration of critical data, the journey of an attack is intricate, yet predictable.
By understanding each link in the attackers’ chain, we can devise strategies, layering defenses that not only counteract but also anticipate threats. From the preliminary precaution of scanning our Docker images to the vigilant watch of web application firewalls and alert systems, every step can be a bulwark against compromise.
This blog seeks to journey through this potential attack chain, delving into each tactic while equipping readers with proactive measures to ensure Kubernetes remains a bastion of efficiency without becoming a gateway for cyber adversaries.
The Detailed Kubernetes Kill Chain
The following section will unravel a potential attack scenario targeting Kubernetes. By walking through this orchestrated chain of events, you will gain a firsthand perspective of how vulnerabilities can be exploited, from the earliest inklings of compromise to the culminating breach.
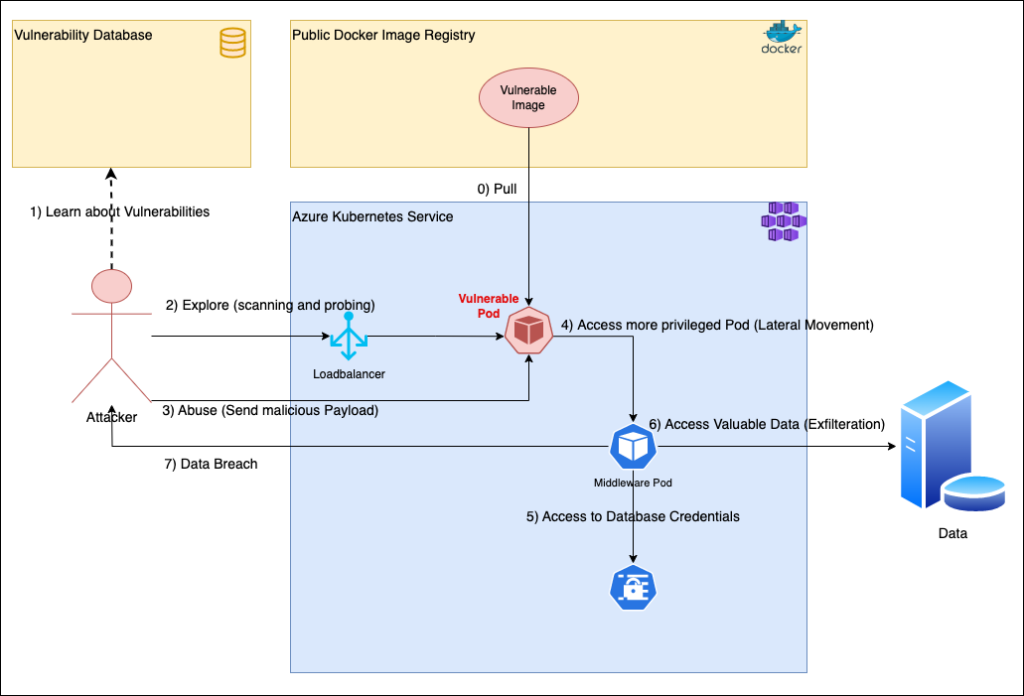
0. Image Vulnerability (Initial Access): The journey of a potential breach often begins innocently. By pulling a Docker image riddled with vulnerabilities, we inadvertently lay the foundation for a potential security compromise. While developers might be seeking efficiency and speed, malicious actors are always on the hunt for such overlooked weak spots.
1. Knowledge Gathering (Reconnaissance): Once a cybercriminal becomes aware of these vulnerable images, they start to scheme. The reconnaissance phase is akin to a burglar scoping out a neighborhood before choosing a house to rob. They seek to understand the lay of the land, studying potential entry points and weaknesses they can exploit.
2. Probing (Discovery): As the attacker zeroes in on the Kubernetes environment, they begin a deeper investigation. They’re essentially trying different keys in the lock, searching for the one that fits. This phase involves detailed scanning and probing, aimed at revealing specific targets and further vulnerabilities within the AKS setup.
3. Payload Delivery (Execution): Having identified a way in, the attacker proceeds to execute their plan. At this stage, they deliver and run a malicious payload inside the targeted container. It’s much like a thief sneaking through an unlocked back door, trying to remain undetected while carrying out their malicious intent.
4. Lateral Movement: Once they gain initial access, it’s not always the endgame. They now look to move sideways or elevate their privileges. In a vast environment like Kubernetes, they aim to transition from their initial entry point to a more privileged pod, one that grants them broader access and more valuable data.
5. Credential Discovery (Credential Access): Every burglar hopes to find a treasure chest or a hidden safe. For cyber attackers, Kubernetes secrets are the equivalent. Discovering these secrets can expose database credentials, opening deeper avenues of access and providing richer pickings.
6. Data Exfiltration (Collection and Exfiltration): With the credentials in hand, attackers can now access databases or other valuable data sources. They methodically gather this data, akin to a thief collecting jewelry and cash, preparing to make their exit with the loot.
7. Data Breach (Impact): The final, often devastating blow – the exfiltrated data is transmitted to the attacker’s domain. The breach is now complete, and the repercussions can be vast, ranging from financial loss to reputational damage.
Fortifying Kubernetes: Our Line of Defense
Enhancing Kubernetes security isn’t just about patching vulnerabilities. It’s about building a multi-layered shield against potential attackers. Let’s explore the protective measures that can fortify our Kubernetes setup.
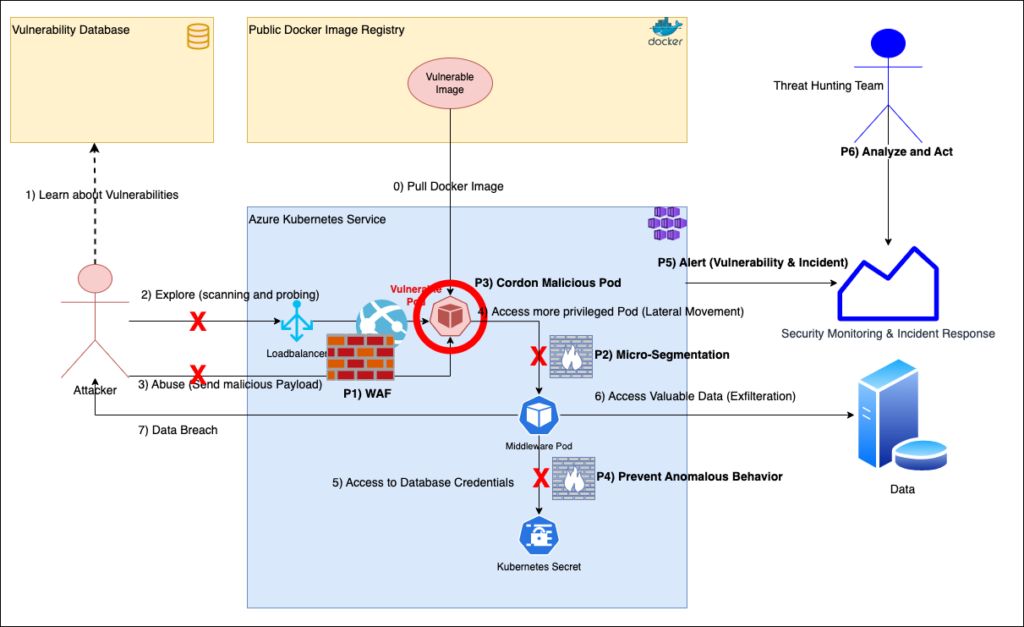
P0) Before even deploying a container, this is our pre-emptive strike against vulnerabilities. By scanning Docker images for known vulnerabilities and ensuring they conform to our organization’s security standards, we drastically reduce the chances of introducing exploitable flaws into our Kubernetes environment. It’s akin to checking the safety of a new household item before bringing it into your home.
P1) WAF (Web Application Firewall): This is our first line of defense, inspecting web traffic, filtering out malicious requests, and blocking potential threats even before they knock on Kubernetes’ door.
P2) Micro-Segmentation: Imagine partitioning your house into zones, each with its security system. Micro-segmentation does this for our digital environment. It not only segments the network but in multi-tenant Kubernetes scenarios, also ensures each user’s or tenant’s access is limited and clearly defined (this is where IAM – Identity and Access Management – comes in).
P3) Cordon Malicious Pod: If a room in your house had a gas leak, you’d seal it off. Similarly, if a pod behaves suspiciously, we can cordon it, preventing it from causing more harm.
P4) Prevent Anomalous Behavior: Tools like NeuVector can learn and whitelist standard behaviors. If anything unusual happens, it gets flagged, much like a security camera spotting an unfamiliar face.
P5) Alert (Vulnerability & Incident): It’s essential to know when something’s amiss. Alert systems notify us of potential vulnerabilities or active threats, prompting immediate action.
P6) Analyze and Act: After an alert, understanding the threat is vital. Using tools like NeuVector, we can inspect, understand, and swiftly act, ensuring minimal damage.
Conclusion
Kubernetes has undoubtedly revolutionized the container orchestration space. However, its widespread adoption also shines a spotlight on its security aspects. By understanding potential attack vectors, visualizing them through frameworks like MITRE ATT&CK, and fortifying our defenses, we can ensure our Kubernetes environments remain robust and secure. After all, in the digital age, being proactive is always better than being reactive.
Disclaimer:
The insights and scenarios discussed in this blog are for educational purposes only. While they provide guidance based on current cybersecurity understanding, no strategy can guarantee complete protection. Always consult with a cybersecurity expert to tailor defenses to your specific needs.
References:
For readers keen on delving deeper into the tactics and techniques that adversaries employ during their attacks, the MITRE ATT&CK framework serves as an invaluable resource. This comprehensive, globally-accessible knowledge base offers insights into known tactics, techniques, and procedures (TTPs) that malicious actors use.
- MITRE ATT&CK Framework: https://attack.mitre.org/
- MITRE ATT&CK Tactics and Techniques: https://attack.mitre.org/tactics/enterprise/
By adopting a comprehensive approach to Kubernetes security, organizations can strike a balance between operational agility and cybersecurity robustness, ensuring they reap the benefits of container orchestration without compromising their digital safety.
