Kubernetes & Service Mesh Security
Zero-Trust in every phase of workloads lifecycle. Strong set of guidelines and tools secure to running and migration of your workload in the cloud and on premise Kubernetes.
Multi-Layer Protection

IAM & Governanace
Zero Trust principle applies on users, services, networks, Docker images and many more things. Our solutions allow running only trusted/known Docker images with trusted/known configurations.
Trust also covers authenticating and authorizing human and machine or service identities. Least priviledge applies on all identities, so only needed access is allowed.

Micro Segmentation
Apply zero-trust in a multi-tenant Kubernetes environment by allowing only trusted/known communications and otherwise disallow the rest.
So, different unrelated workloads runnig and sharing Kubernetes resources are kept isolated from network perspective.
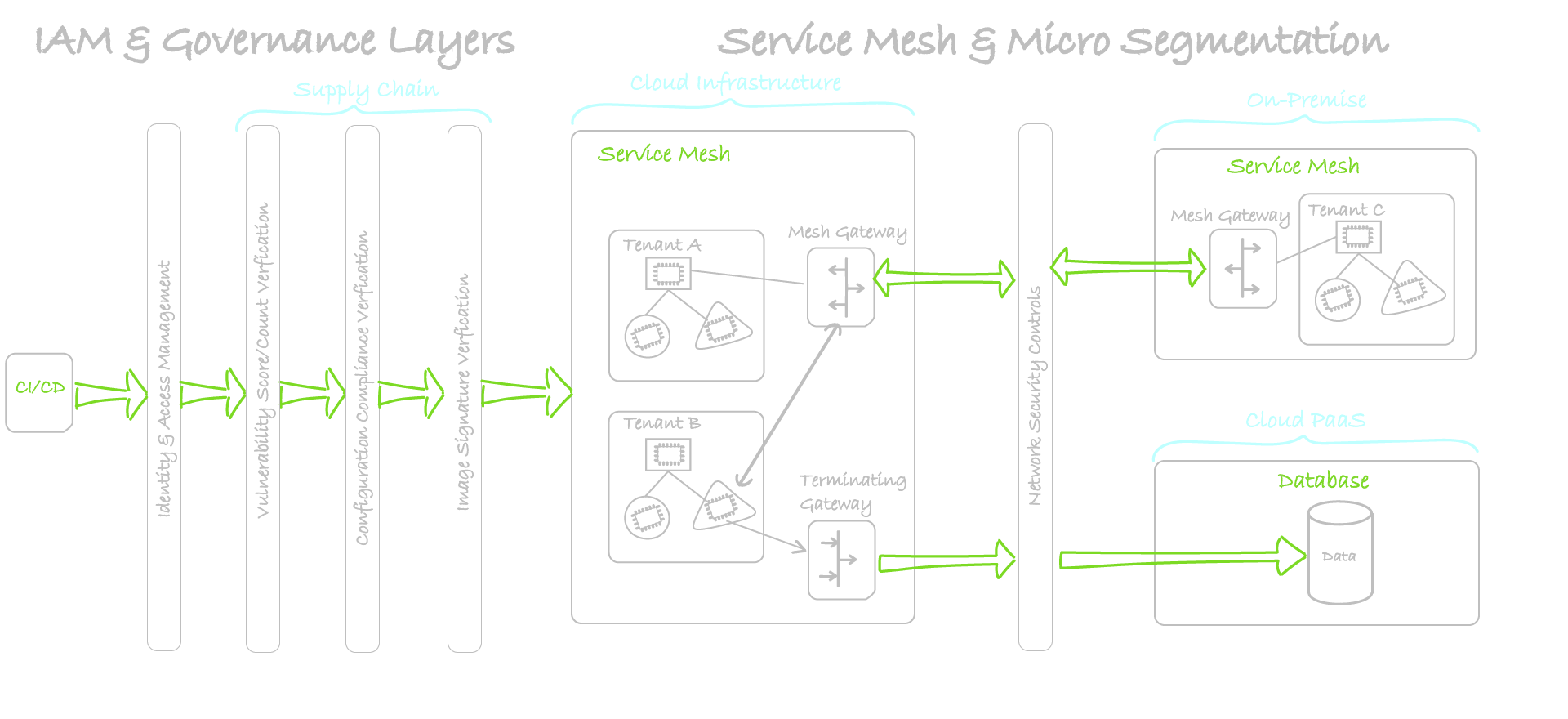
Service Mesh
Zero trust with Service Mesh enriches your security journey with automated encryption in transit.
Service mesh offers identity based authentication and authorization: So, for example, you can allow service A to connect to service B but not service C.
It enables connecting to applications and PaaS databases in the cloud and on-premise.
Vulnerability Management

Vulnerabilities are discovered and published continuously. Our solution informs you about newly discovered vulnerabilities and their score.
Based on your custom policy, you may decide to disallow specific workloads, when they include specific count of certain vulnerability score.
IAM
IDENTITY AND ACCESS MANAGEMENT
Our IAM solution includes purpose-oriented authntication and authorization concept.
Human users use SSO through integration with user directories, while services and machines use special authentication methods to avoid effort and headache related to management of static secrets (creation, rotation, deletion and access monitoring).
We design IAM least priviledge design principle to allow different identities to achieve only intended tasks.

Automated Compliance Verification
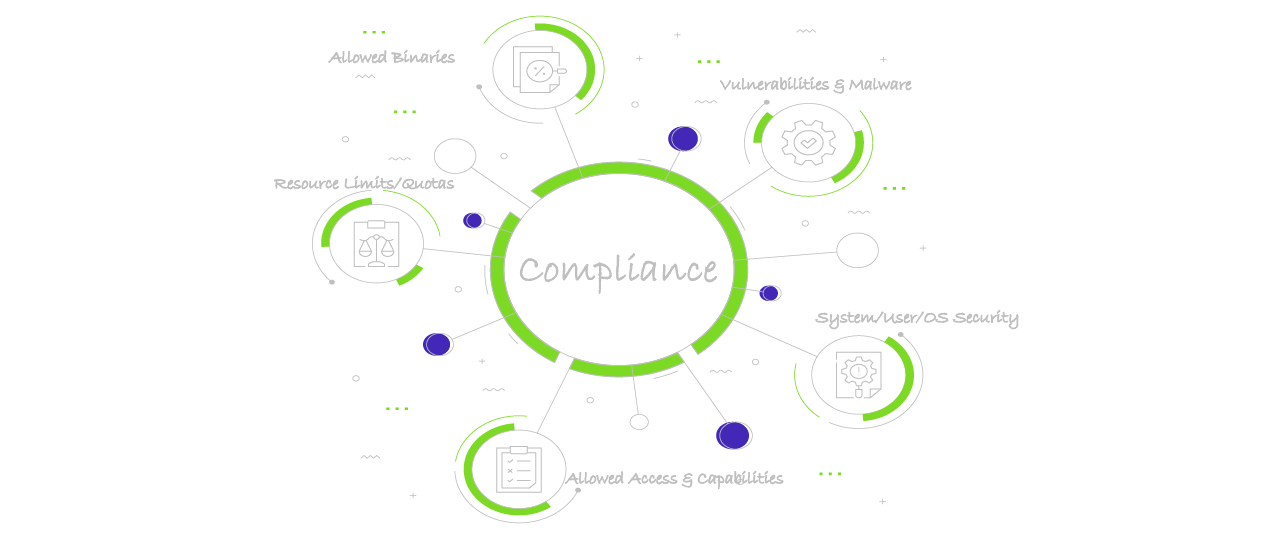
Our solution applies zero-trust by allowing only trusted/known Kubernetes workload configuration. For example, limiting quotas and cpu and memory, preventing root user or priviledge escalation in pods/containers, disallowing Linux capabilities, only allow container images from whitelisted Docker registries and many more configurable rules.
Image Signature
During CI (Continuous Integration), software, binary libearies, and Docker base images are scanned to fined weaknesses and vulnerabilities. Then, a kind of trusted Docker images are created and pushed to private Docker registry.
Our solution applies zero-trust in this context by signing Docker images created during CI. Then, after verifying the signature, only allow those to run in Kubernetes.
Other trusted Docker images created by other providers can be whitelisted, too.
Micro-Segmentation
When multiple tenants (teams, products or services) share Kubernetes infrstructure, it is essential to isolate those workloads from network, process and file system perspectives.
We support one of the best isolation methods by applying another zero-trust approach; Namely, to allow trusted/known communications and behavior inside Kubernetes. Otherwise any other network, process or file access is simply disallowed.
Service Mesh
Service Mesh enriches security zero-trust in terms of data protection and micro-segmentation. Our solution supports simple to use features that increase security and save manual effort through automation.
- Encryption in transit: so all communications among services participating in the mesh will be encrypted end to end.
- Identity based authentication and authorization: So, you can allow service A to connect to service B but not service C.
- Automated rotation of leaf certificates.

Threat Detection and Prevention

With Zero-Trust security, any unknown behaviour of Malware is detected and automatically prevented. Following prevention and protection are possible:
- Network access to unusual internal and external destinations.
- Start of not whitelisted binaries.
- Access to unusual files and directories.
- Privilege Escalation.
Need Consulting? Contact Us Now!
We will be happy to listen to your challenges and wishes. Please describe briefly, how we can help you.
