Secure Secret Management
Solution Overview
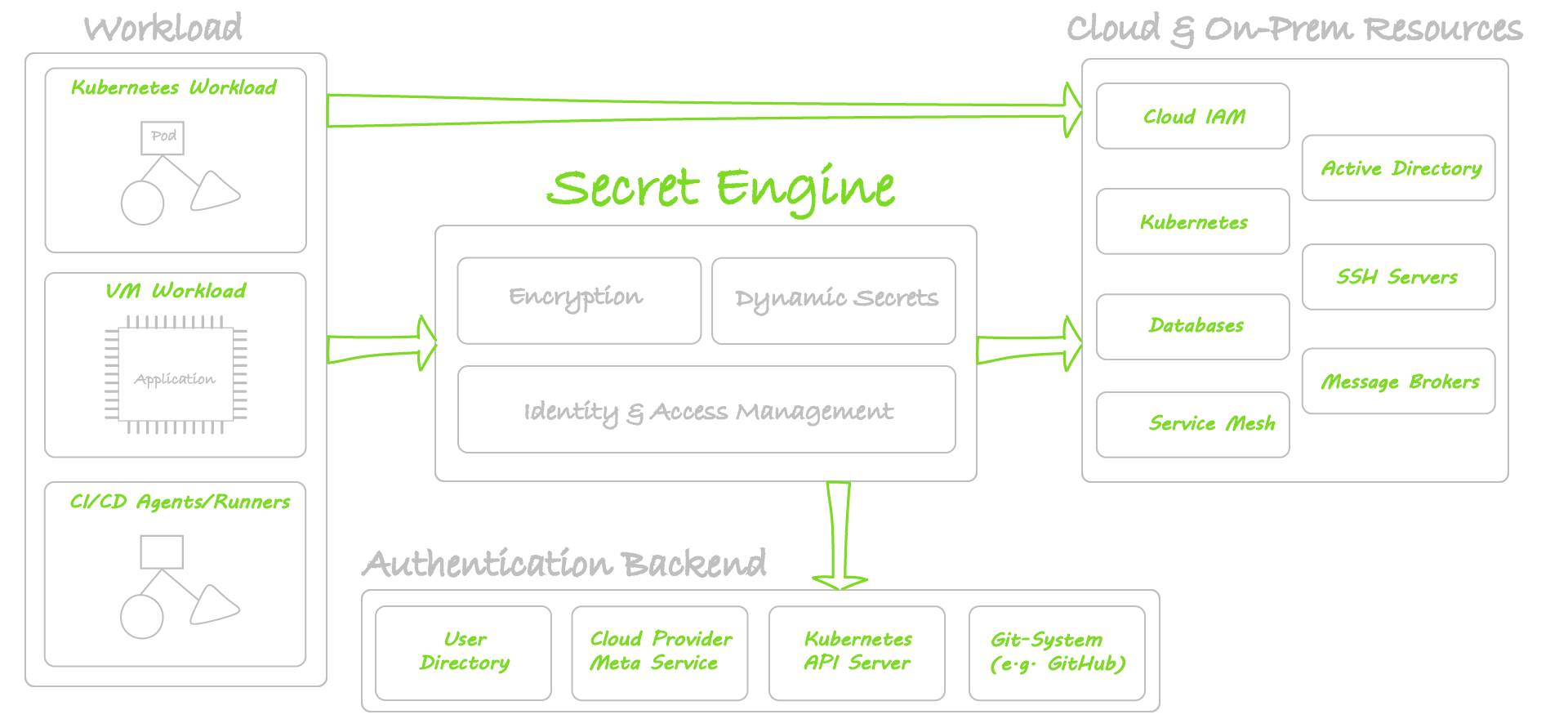
Zero-Trust Principle allows secure access to workloads and resources running in cloud and on-premise. Our set of guidelines and tools enable secure secret management.
- Dynamic Secrets: Automated & Secure Creation, Handover, and Rotation of Secrets.
- No Downtime or any Maintenance Window needed during Secret Rotation.
- Authenticate Services through Integration with your Trusted 3rd Party Services such Kubernetes, GitHub, GitLab, Azure AD, Cloud IAM…etc.
- Least Priviledge Principle always Apply.
- Many Backend Systems Supported (Databases, Brokers, User Directories, Cloud IAM…etc.)
Need Consulting? Contact Us Now!
We will be happy to listen to your challenges and wishes. Please describe briefly, how we can help you.